The so-called biometric technology is the combination of computer and optical, acoustic, biosensor and biostatistical principles, using the inherent physiological characteristics of the human body (such as fingerprints, faces, irises, etc.) and behavioral features (such as handwriting). , voice, gait, etc.) to identify individuals.
Many biometric identification technologies have emerged, such as fingerprint recognition, palm geometry recognition, iris recognition, retina recognition, facial recognition, signature recognition, and voice recognition. However, some of the high-tech biometric identification methods are still in the experimental stage. We believe that with the rapid advancement of science and technology, more and more biometric technologies will be applied to real life.
Fingerprint recognition for biometrics: There are several ways to implement fingerprint recognition. Some of them follow the traditional methods used by the public security department to compare the local details of fingerprints; some are identified directly by all features; others use more unique methods such as the rippled edge pattern of fingerprints and ultrasound. Some devices can measure finger fingerprints on the fly, while others can't. Among all biometric technologies, fingerprint recognition is the most widely used one. Fingerprint recognition is more suitable for indoor security systems, because there are sufficient conditions for users to provide explanations and training, and the system operating environment is also controllable. Due to its relatively low price, small size (which can be easily integrated into the keyboard) and easy integration, almost all of the applications in the workstation security access system are fingerprint recognition.
There are four main types of fingerprint image acquisition technologies: optical scanning devices (such as micro prism arrays), temperature difference sensing fingerprint sensors, semiconductor fingerprint sensors, and ultrasonic fingerprint scanning.

Biometric recognition of palm geometry: Palm geometry recognition is performed by measuring the physical characteristics of the user's palms and fingers, and advanced products can also recognize three-dimensional images. As an established method, palm geometry recognition not only has good performance, but also is convenient to use. It is suitable for occasions where the number of users is large, or users do not use it often, but it is easy to accept when used. The accuracy of this technique can be very high, if needed, while flexibly adjusting the performance of biometric technology to accommodate a wide range of usage requirements. Hand readers are used in a wide range of applications and are easily integrated into other systems, making them the technology of choice for many biometric projects.
Voice recognition for biometrics: Voice recognition is a technique for identifying by analyzing the physical characteristics of the user's voice. Nowadays, although some voice recognition products have entered the market, they are not very convenient to use, mainly because the sensor and human voice are very variable. In addition, compared to other biometric technologies, the steps used are more complicated and inconvenient in some cases. A lot of research work is underway, and we believe that voice recognition technology will make significant progress.
Retinal Recognition for Biometric Recognition: Retinal recognition uses a low-intensity light source from an optical device to scan a unique pattern on the retina. There is evidence that retinal scanning is very accurate, but it requires the user to look at the receiver and stare at it. This is very inconvenient for people wearing glasses, and the distance from the receiver is very close and uncomfortable. So although the retina recognition technology itself is very good, the user's acceptance is very low. As a result, this product was redesigned in the 1990s to enhance connectivity and improve the user interface, but it is still a non-mainstream biometric product.
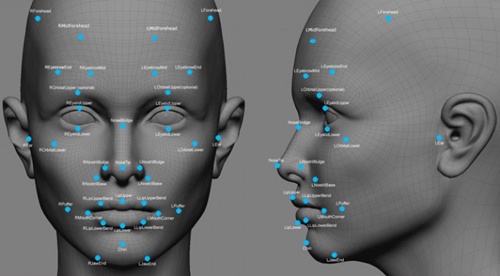
Biometric facial recognition: This is a fairly attractive technique and its performance is often misunderstood. There are often some exaggerated remarks about facial recognition, but it is actually very difficult to achieve. Comparing two static images is one thing. Finding and confirming someone's identity in the crowd without attracting the attention of others is another completely different matter. Some systems claim to be able to do the latter, but they actually do the former, which is not actually biometric. The appeal of facial recognition is easy to understand from the user's point of view, but expectations of this technology should be more realistic. Facial recognition has rarely been successful in practical applications. But once it overcomes technical barriers, it will become an important biometric method. In 2012, Wuhan Public Security is constructing a high-precision portrait recognition system that can match 100 million images in one second and instantly identify suspects.
The system collects images mainly through 250,000 video probes installed at urban road junctions, on both sides, and on buses. Video surveillance will accurately capture the portraits of the suspects in the background data and lock the suspects within seconds. The system will be put into practical use in March 2013.
Facial recognition technology is used in many areas:
1. Enterprise, residential security and management. Such as face recognition access control attendance system, face recognition security door and so on.
2. Electronic passport and ID card.
3. Public security, justice and criminal investigation.
4. Self-service.
5. Information security. Such as computer login, e-government and e-commerce.
Vein recognition for biometric recognition: vein recognition, using near-infrared reading of the vein mode, comparison with the stored vein pattern, and identification technology for personal identification. The working principle is that the blood flowing in the human finger can absorb the light of a specific wavelength, and the finger is irradiated with the specific wavelength light to obtain a clear image of the finger vein. Using this inherent scientific feature, the acquired image will be analyzed and processed to obtain the biometric characteristics of the finger vein, and the obtained finger vein feature information will be compared with the previously registered finger vein feature to confirm the registrant. identity of.
The vein recognition system first obtains the individual vein distribution map through the vein recognition instrument, extracts the feature value from the vein distribution map according to the special comparison algorithm, and acquires the image of the finger, the palm and the back vein of the hand through the infrared CCD camera, and stores the digital image of the vein in the vein image. In computer systems, feature values ​​are stored. When the vein is compared, the vein map is taken in real time to extract the feature values, and the advanced filtering, image binarization and refinement methods are used to extract the features of the digital image, and the venous feature values ​​are stored in the host, and a complex matching algorithm is used. The venous features are matched to identify individuals and confirm their identity.
In the face of huge market development, the new generation of access control products that embed vein identification products into the access control system are becoming more mature with the preparation of previous years. In order to seek the intelligent development of the access control system and catch up with the rapidly developing trains in the access control market, enterprises with vein identification technology in China are ready to go and seek blasting development. Based on this, we will develop a series of products suitable for the Chinese market and successfully apply them to industries or departments such as prisons, family planning, coal mines, information security, finance, education, and social security. At the same time, many access control companies are also opening up the blue ocean with the introduction of "venous" as the access control market.
Gait recognition of biometrics: gait recognition, using the camera to collect the image sequence of the human walking process, and processing and comparing with the stored data to achieve the purpose of identification. The Institute of Automation of the Chinese Academy of Sciences has conducted some research. As a biometric technology, gait recognition has the unique advantages that other biometric technologies do not have, that is, the recognition potential in the case of long distance or low video quality, and the gait is difficult to hide or disguise. Gait recognition is mainly for the analysis of moving image sequences containing humans, usually including three stages: motion detection, feature extraction and processing, and recognition classification.
However, there are still many problems that restrict its development. For example, the angle of shooting changes, the clothing of the identified person is different, and there are different things. When the captured image is extracted, the recognition effect will be changed. However, this identification technology can achieve long-distance identification with outstanding performance in active defense. If you can break through the existing constraints, it will certainly be useful in practical applications.
related articles:
Ten key technologies for biometrics that have to be known
Face recognition core algorithm and technical analysis
Comprehensive discussion of the principles and applications of biometrics and principles. Focus on several widely used and promising biometric solutions.
Disposable surgical masks are made of nonwoven material, including filter layer, mask belt and nose cheek. They are generally disposable and can block particles larger than 5 microns in diameter.Especially surgical masks, the resistance to bacteria and viruses is strong, can effectively filter the virus or bacteria attack the respiratory tract, also can avoid the virus and bacteria to others.
And the ordinary mask is not generally disposable, the material is more, there is cotton mask, there is also non-woven cloth mask.The main effect is to keep warm more, still can block the dust droplet of part, but the ability of general antivirus is lesser, cannot prevent bacterium or virus to invade respiratory tract.
Disposable medical mask,Mask medical,Medical masks,Facemask
YFJ TECHNOLOGY (HK) CO.,LIMITED , http://www.yfjpower.com